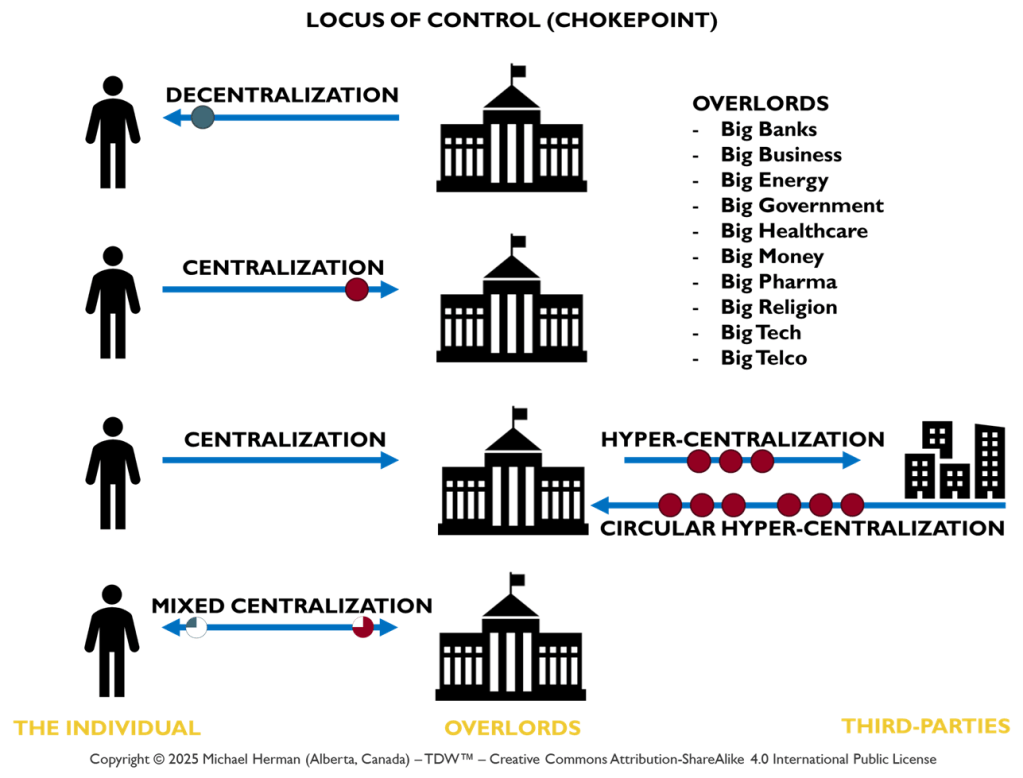
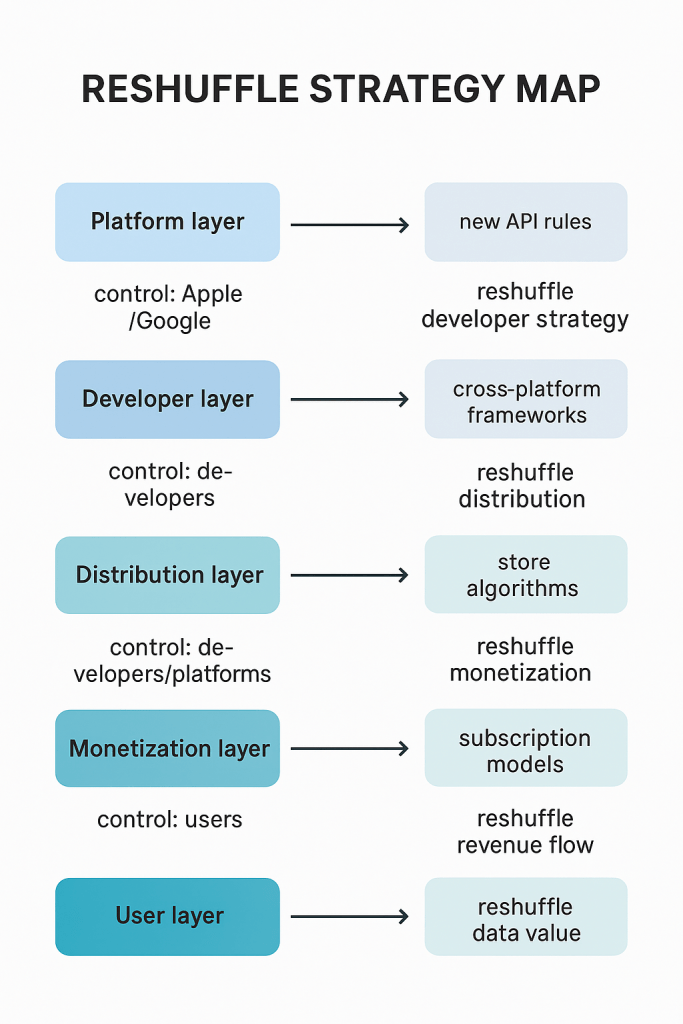
Create your own magic with Web 7.0 AgenticOS™. Imagine the possibilities.
Copyright © 2025 Michael Herman (Bindloss, Alberta, Canada) – Creative Commons Attribution-ShareAlike 4.0 International Public License
ChatGPT: I read Christopher Allen’s original “Ten Principles” (2016) and pulled a short set of modern, standards- and ecosystem-aware sources (W3C DID / Verifiable Credentials, Trust Over IP, Sovrin, EBSI) to make sure the updated set reflects real-world progress since 2016. (lifewithalacrity.com)
Below is a proposed updated & expanded collection of Principles of Self-Sovereign Identity — 16 principles grouped into themes, each with a short explanation and why it matters today. After the list I include a compact mapping to Allen’s original ten so you can see continuity.
Updated Principles of Self-Sovereign Identity 7.0
Core: sovereignty & agency
- Existence & Agency — People (and other identity subjects) have an independent existence and agency over their identifiers and claims. Identity systems must start from the person (or subject) and preserve that agency. (recovers Allen’s Existence/Control). (lifewithalacrity.com)
- User Control (Agency in Practice) — Users must be the operational controllers of their identifiers, credential stores (wallets/agents), and consent decisions — including fine-grained, revocable consent. Control must be meaningful (usable) not just theoretical. (walt.id)
Technical interoperability & standards
- Standards-based Interoperability — Implementations should rely on open standards (e.g., W3C Decentralized Identifiers and Verifiable Credentials) to enable global, cross-vendor interoperability of identifiers, credentials, and presentations. Standards provide portability and composability across ecosystems. (W3C)
- Protocol & Architectural Openness — Protocols (DID methods, messaging like DIDComm, wallet APIs) and reference architectures (e.g., Trust Over IP stack) must be open and modular so ecosystems can interoperate while allowing local innovation and governance. (Trust Over IP)
Privacy, minimal disclosure & security
- Data Minimization & Selective Disclosure — Disclosures must reveal the minimum data necessary; support selective disclosure, zero-knowledge proofs, and anonymous/pseudonymous modes to reduce correlation and surveillance risks. (lifewithalacrity.com)
- Privacy by Design & Accountability — Systems should be designed for privacy by default and include accountability mechanisms (consent logs, auditable policies) so misuse can be detected and remedied.
- Security & Resilience — Identity systems must provide robust cryptographic security, threat-resistant key management (including social recovery and hardware wallet options), and resilience to compromise, outages, and future threats (e.g., post-quantum planning).
Lifecycle, governance & legal
- Persistence & Manageable Lifecycle — Identities and credentials should be persistent as the holder requires, with clear, manageable lifecycle operations (issuance, renewal, revocation, expiry, archival, “right to be forgotten”). Allen’s persistence principle expanded to operational lifecycle. (lifewithalacrity.com)
- Recoverability & Continuity — Systems must provide practical and secure recovery mechanisms (social recovery, delegated guardianship, legal recovery paths) so loss of keys or devices does not destroy access to identity or essential services.
- Governance, Trust Frameworks & Legal Compatibility — Identity ecosystems require transparent governance and legal frameworks (e.g., ToIP governance, regional trust frameworks like EBSI) to mediate disputes, define liability, set assurance levels, and enable cross-jurisdictional recognition. (Trust Over IP)
Ecosystem & practical adoption
- Usability & Accessibility — Real self-sovereignty only exists when interfaces, error recovery, and flows are usable by non-experts and accessible to people with disabilities and diverse contexts (language, literacy, device constraints).
- Interoperability with Existing Systems — SSI should interoperate with existing eID, legal, financial, and institutional systems (bridging, translation, hybrid trust models) so real services can use SSI credentials today. (EBSI and other national/regional deployments show this direction). (European Commission)
- Assurance, Provenance & Auditability — Verifiers need to rely on trustworthy evidence. Credential schemes should include provenance metadata, assurance levels, and revocation mechanisms so verifiers can make informed decisions without central control. (W3C)
Ethics, inclusivity & future proofing
- Human Rights & Ethical Use — Identity systems must protect human rights (privacy, freedom of association, non-discrimination) and explicitly avoid enabling oppression, surveillance, or exclusion; risk assessments and ethical review should be part of deployment.
- Inclusivity & Non-Discrimination — Systems must be designed to include people without formal credentials, low-resource settings, refugees, and marginalized communities; they must not require devices, connectivity, or literacy levels that exclude vulnerable populations.
- Extensibility & Future-proofing — The model must support non-human subjects (devices, organizations, agents), evolving cryptography, new proof techniques, and new governance models — i.e., it must be extensible without breaking user sovereignty. W3C specs and ecosystem work (Sovrin/Hyperledger/ToIP) show that extensibility is central to adoption. (Sovrin)
Short rationale & evidence
- Standards matter now. Since Allen’s post, the W3C DID and Verifiable Credentials work have become de-facto standards shaping implementations; any modern principles set must call out standards-based interoperability. (W3C)
- Governance & trust frameworks are essential. Technical primitives alone don’t create real trust for large-scale public or cross-border use — frameworks like Trust Over IP and regional initiatives (EBSI) show the need for human/legal/governance layers. (Trust Over IP)
- Practical recovery and UX are blockers for adoption. The community has learned that without recoverability and usable wallets/agents, people lose keys and services fail. That motivates explicit Recoverability and Usability principles. (See ecosystem projects and wallet tooling). (walt.id)
Mapping to Allen’s Original 10
To keep continuity: most of Allen’s ten are preserved but expanded into modern categories:
- Allen’s Existence, Control, Access, Transparency, Persistence, Portability, Interoperability, Consent, Minimalization, Protection are preserved and appear across the updated list (Existence & Agency; User Control; Access incorporated into Usability/Recovery; Transparency → Architectural Openness and Governance; Minimalization → Data Minimization; Protection → Security & Human Rights). See Allen original. (lifewithalacrity.com)
Reference: https://chatgpt.com/s/t_692bd672442881919413c87440f25ce1