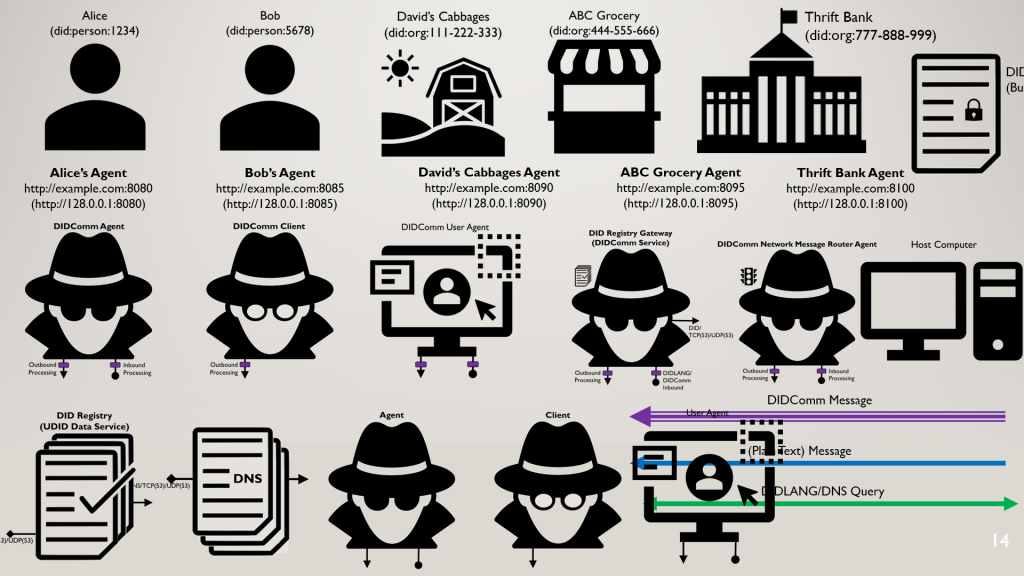
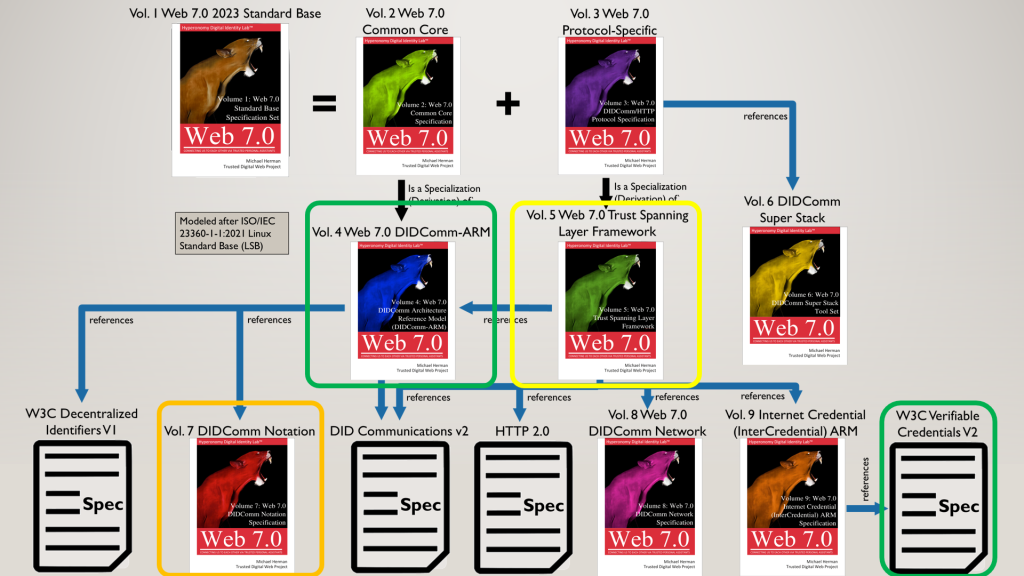
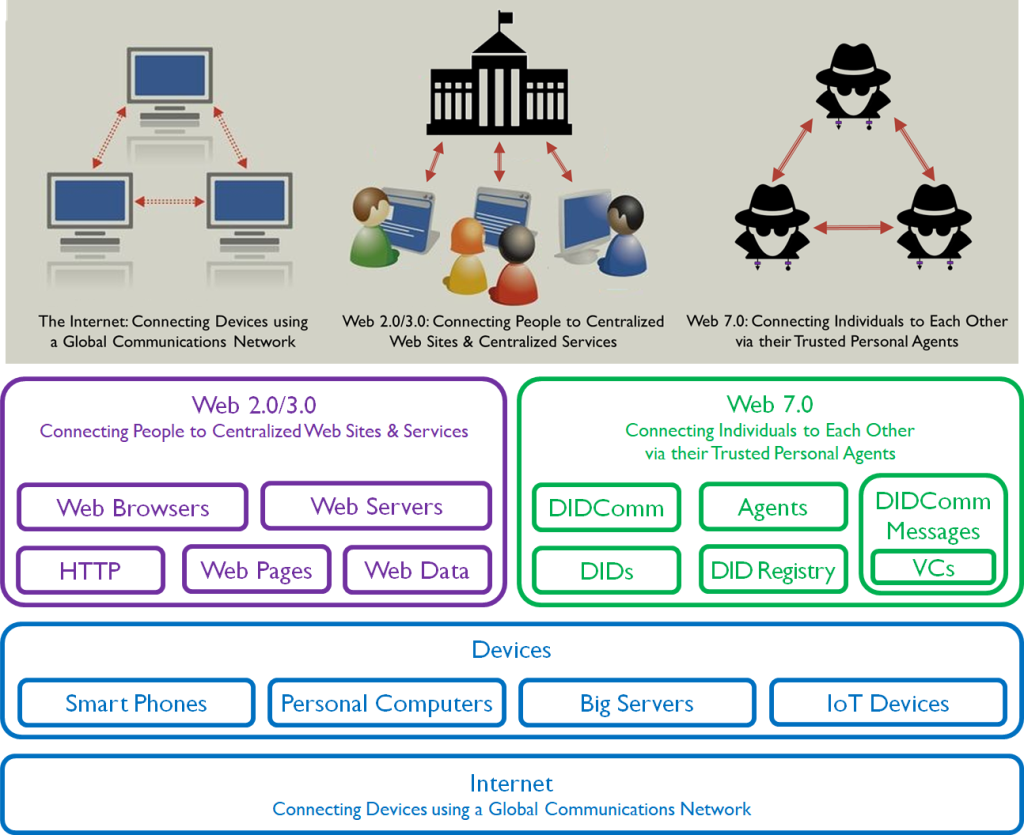
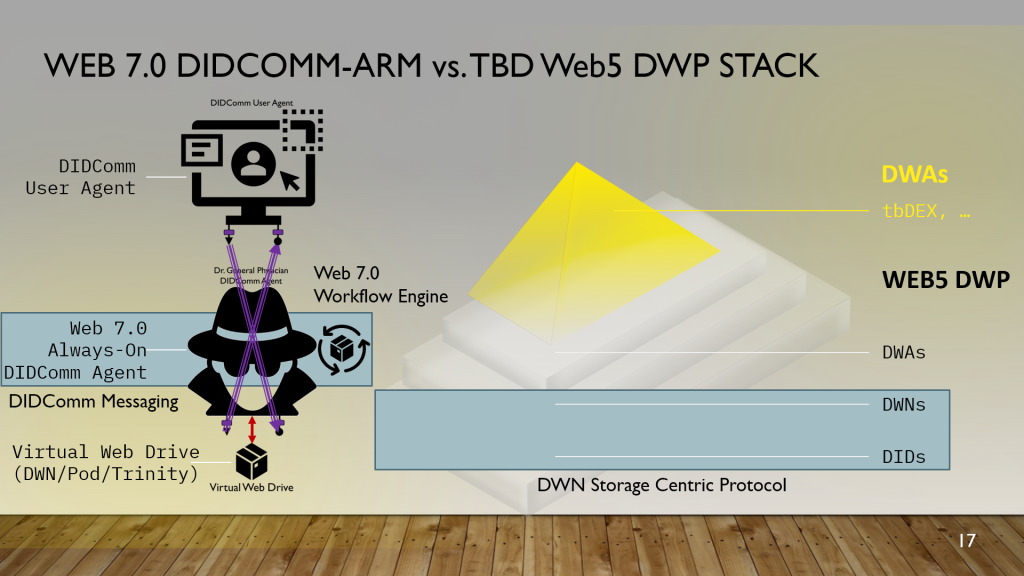
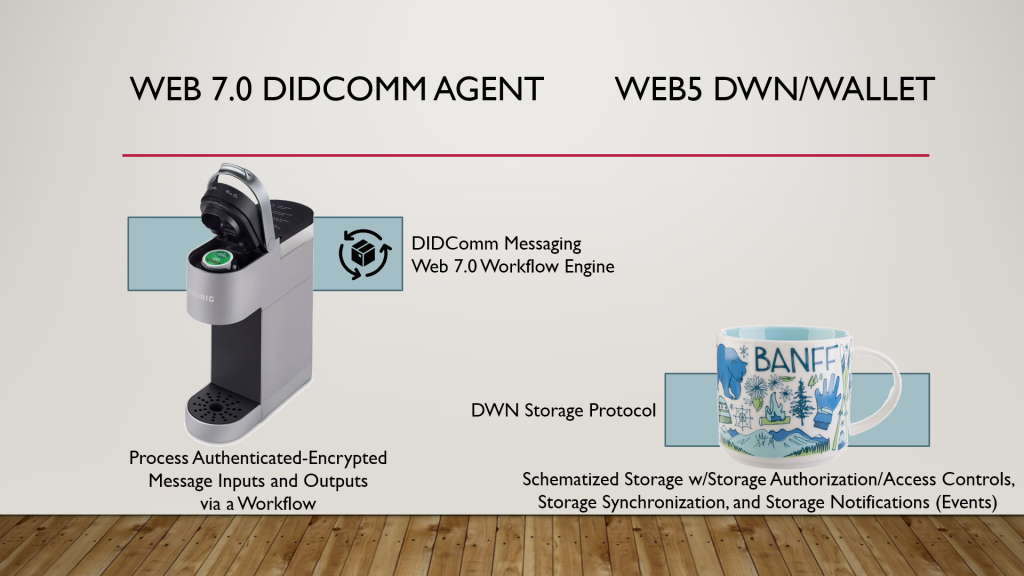
Web 7.0 is a universal, open-source solution for the Internet’s digital identity and trust problems.

The Internet was created 40 years ago. The World Wide Web application, running on top of the Internet, was created more than 30 years ago. Neither the Internet nor the WWW included built-in support for each person to have their own unique, universal digital identity and, hence, no built-in ability to support secure, authentic, and trusted communications. Every website and mobile app was left to develop, test, and manage its own digital identity solution.
Web 7.0 is a universal, open-source solution for the Internet’s digital identity and trust problems. Web 7.0 is a decentralized operating system for building resilient, secure, and trusted systems on top of the Internet using decentralized identity, trusted personal agents, and verifiable credentials.
Key use cases include:
- Safe storage and transmission of medical records (lab results, disgnostic imaging, doctor’s notes, vaccinations)
- Reliable, secure, and trusted end-to-end processing of business transactions (purchase orders, invoices, waybills, delivery confirmations)
- Secure collaboration (instant messaging, presence, and file transfers)
- Authenticated exchange of higher-education, professional and skills-based credentials
The goals of the Web 7.0 community are to support, promote, protect, and curate the Web 7.0 software and hardware ecosystem: Web 7.0 operating system software, standards, and specifications.

More details can be found here: