Copyright (c) 2016 Michael Herman (Alberta, Canada) – Creative Commons Attribution-ShareAlike 4.0 International Public License
https://creativecommons.org/licenses/by-sa/4.0/legalcode
How do we think about how we work? We rely on a few simple processes. Here is a list:
- Progressive Improvement & Learning Process (PILP)
- Continuous Transformation Process (CTP)
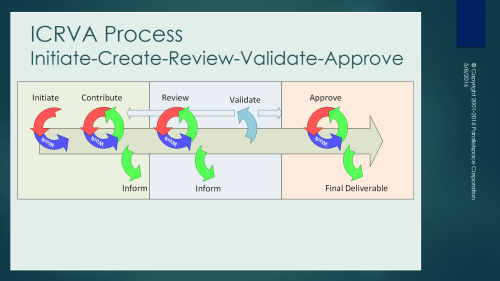
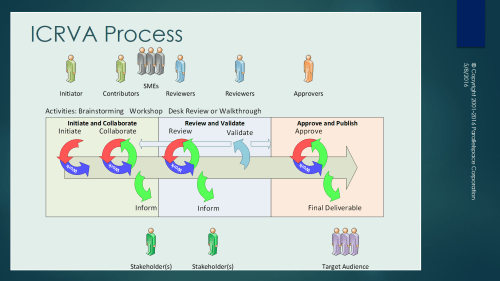
- Deliverable Review: Initiate, Create, Review, Validate & Approve Process (ICRVA Process – “I crave a” Process)
- Purpose: Awareness, Knowledge, Understanding, and Wisdom
Many thanks go to Alison Williams for helping me to clarify the Continuous Transformation Process (CTP).
Michael Herman (Toronto)
Progressive Improvement through Continuous Transformation
Progressive Improvement & Learning Process (PILP)
Continuous Transformation Process (CTP)
Deliverable Review
Initiate, Create, Review, Validate & Approve (ICRVA) Process (“I crave a” Process)
The roles in the ICRVA process are based on the RACI matrix of responsibilities.
Content Purpose
– when writing a whitepaper or creating a new presentation
- Awareness (An Overview of what is being described (Information))
- Knowledge (The “What” of what is being described)
- Understanding (The “How” of what is being described)
- Wisdom (Deep Knowledge and Understanding acquired through Experience)
By wisdom a house is built, and by understanding it is established; by knowledge the rooms are filled with all precious and pleasant riches. A wise man is full of strength, and a man of knowledge enhances his might, for by wise guidance you can wage your war, and in abundance of counselors there is victory. Wisdom is too high for a fool; in the gate he does not open his mouth. (Proverbs 24:3-7)
Intended Audience Statement (Example)
The intended audience for this tutorial about Structured Credentials is a broad range of professionals interested in furthering the application of Verifiable Credentials technology for use in software apps, agents, and services. The primary audience includes software architects, application developers, and user experience (UX) specialists; as well as people involved in a broad range of standards efforts related to decentralized identity, verifiable credentials, and secure storage.
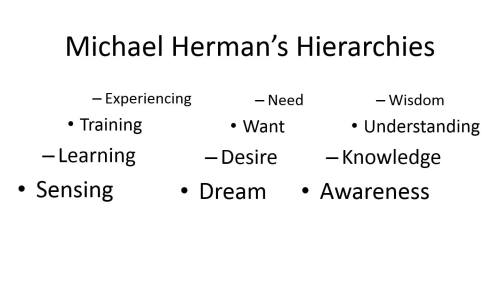
Michael Herman’s Hierarchies
- Awareness – Knowledge – Understanding – Wisdom
- Dream – Desire – Want – Need
- Sensing – Learning – Training – Experiencing
- Keywords – (Controlled) Vocabulary – Glossary – Dictionary – Taxonomy – Ontology
Product Management: 3 Prioritization Levels
- Need to have
- Nice to have
- *Neat* to have
Scalability Levels

Best regards,
Michael Herman (Toronto)
Parallelspace Corporation
mwherman@parallelspace.net





Pingback: ARMs for Metadata-Driven LOB apps: SharePoint 2013/SharePoint 2016 | hyperonomy.com
Pingback: Crossing the EA Chasm: Annotating Your EA Model with RACI Roles | hyperonomy.com - digital intelligence
Pingback: #Graphitization of the Amazon Leadership Principles (introducing Personal Leadership Principle Maps) – Iteration 1 | hyperonomy.com - digital intelligence
Pingback: Technology Adoption Models: A Comprehensive Guide | hyperonomy.com - digital intelligence