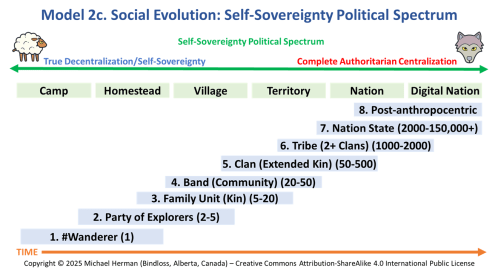
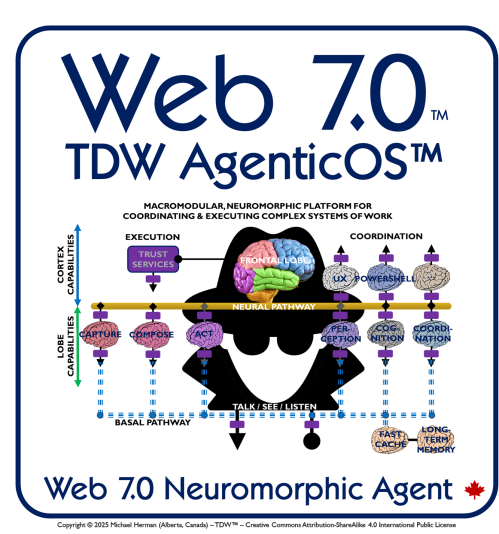
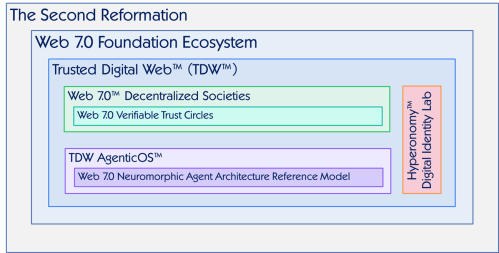
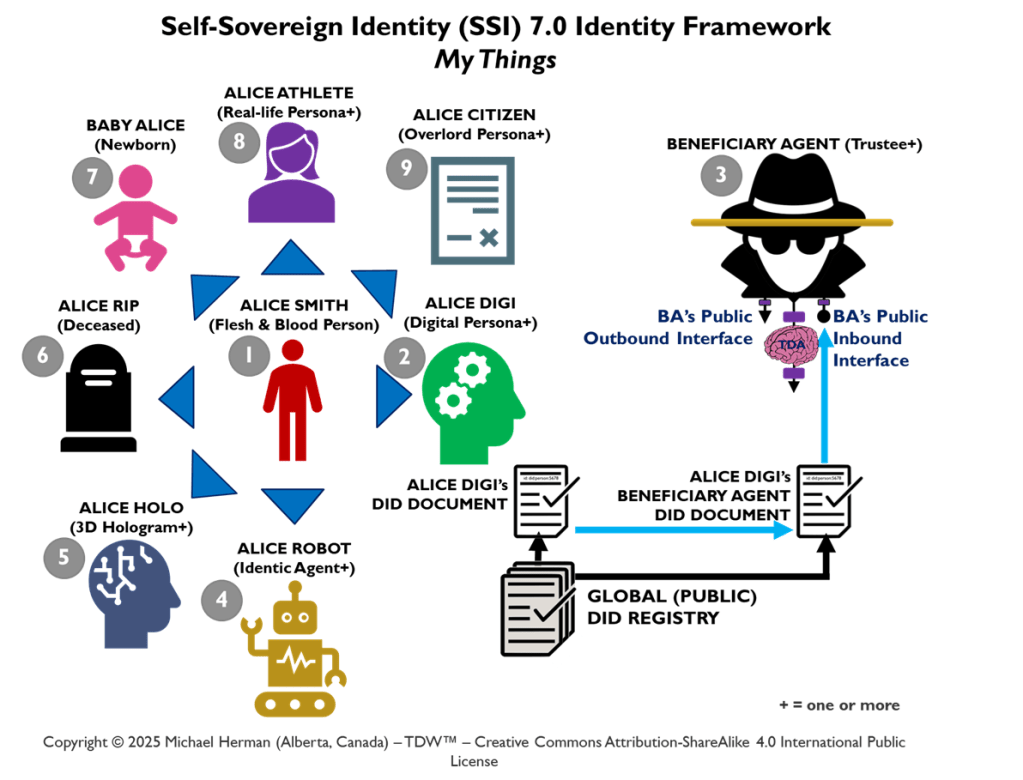
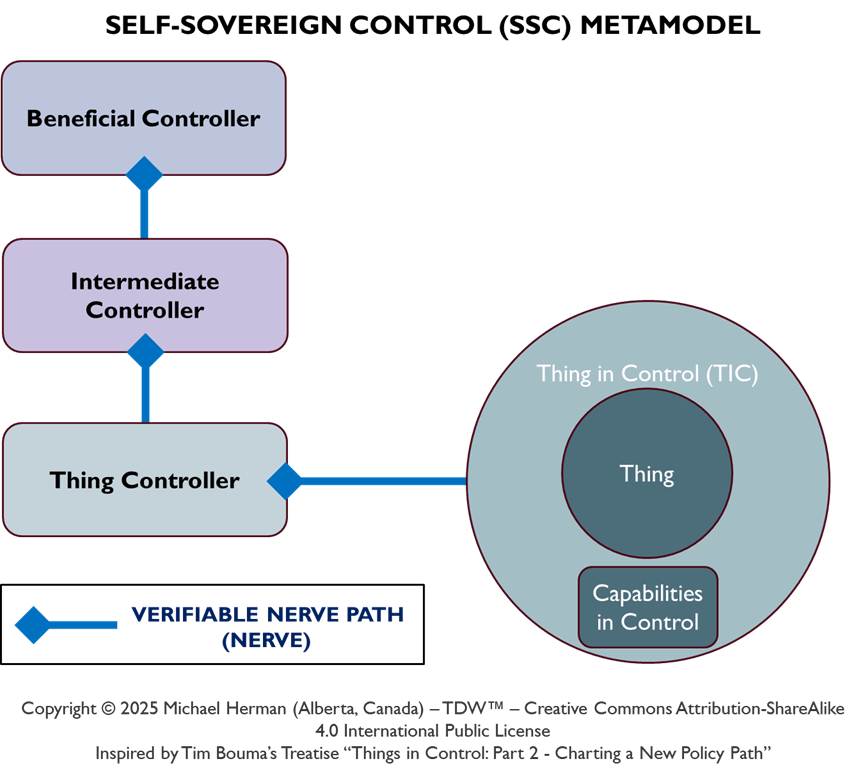
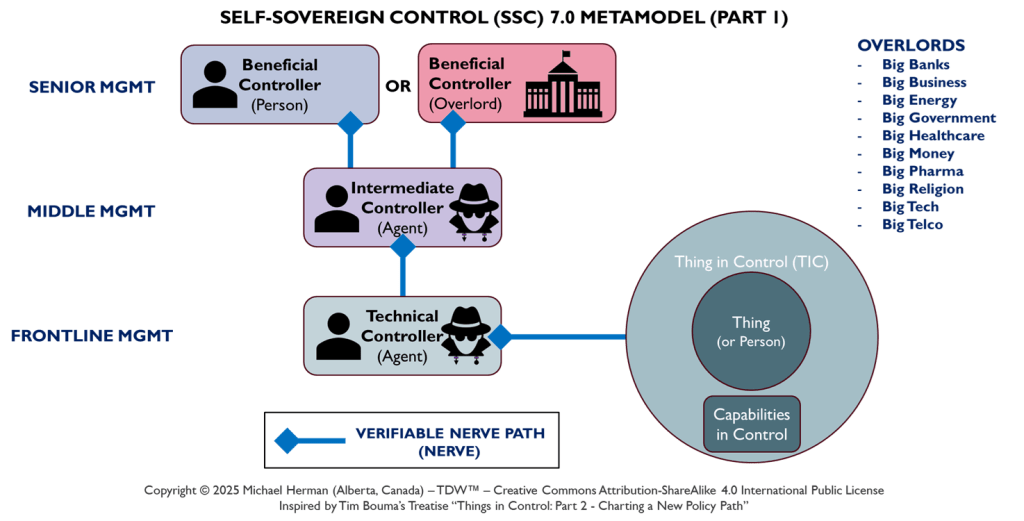
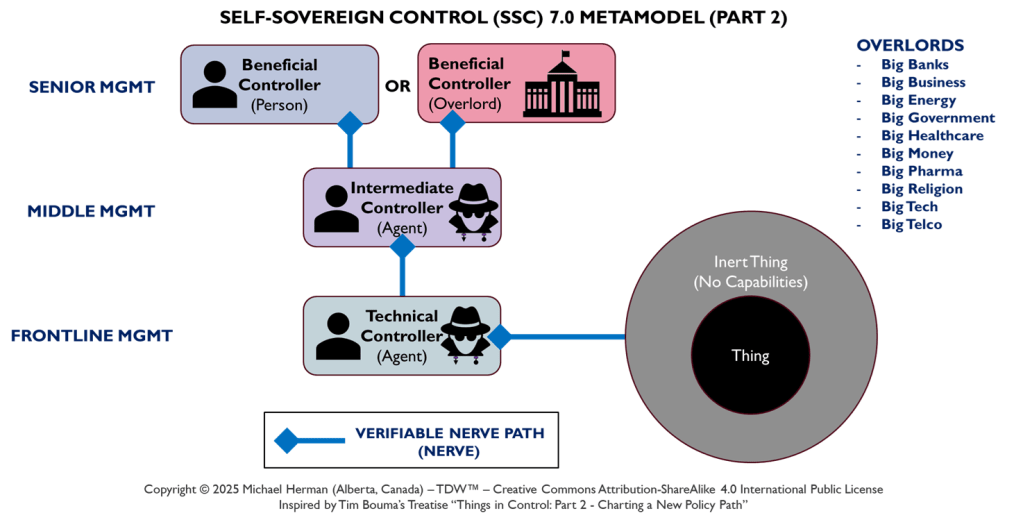
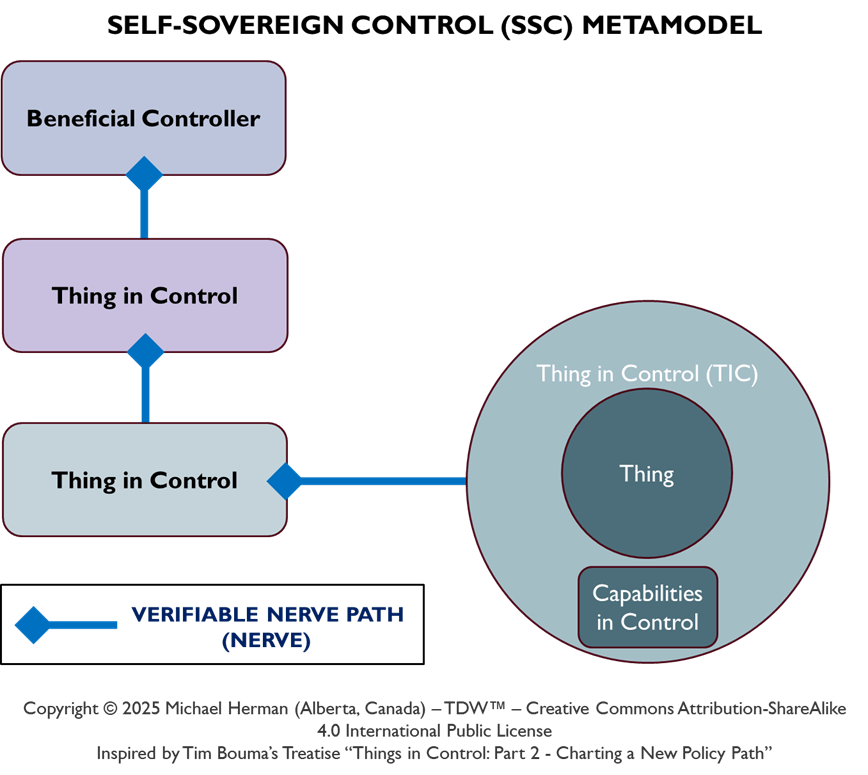
Copyright © 2025 Michael Herman (Bindloss, Alberta, Canada) – Creative Commons Attribution-ShareAlike 4.0 International Public License
The War of 1812 was a conflict fought from 1812 to 1815 primarily between the United States and Great Britain, with fighting concentrated in North America and at sea. It’s often described as a “second war of independence” by Americans and a defensive war by British North America (today’s Canada).
1. Why the War Happened (Causes)
There wasn’t a single cause, but several overlapping ones:
🇬🇧 British actions
- Impressment: The British Royal Navy forcibly took sailors—many of whom were American—from U.S. ships to serve in the British navy.
- Trade restrictions: Britain limited U.S. trade with France during the Napoleonic Wars through blockades and orders in council.
🇺🇸 American motives
- National honor & sovereignty: Many Americans felt Britain was treating the U.S. like a former colony.
- Westward expansion: The U.S. accused Britain of supporting Indigenous resistance to American expansion in the Northwest Territory.
- War Hawks in Congress: Young politicians (like Henry Clay) pushed for war, some believing Canada could be easily conquered.
🪶 Indigenous resistance
- Indigenous nations, led in part by Tecumseh, opposed U.S. expansion and often allied with Britain, seeing them as the lesser threat.
2. Who Fought
- United States
- British Empire
- British North America (Upper & Lower Canada) – militias and settlers
- Indigenous confederacies allied with Britain
Notably, Britain was preoccupied with Napoleon in Europe, which limited resources early in the war.
3. Major Campaigns & Battles
🇨🇦 Canadian Front
- American invasions of Canada (1812–1813) failed.
- Key battles:
- Queenston Heights (1812) – British and Indigenous forces repel U.S. invasion.
- Battle of the Thames (1813) – U.S. victory; Tecumseh killed.
- Canadian militias played a major role in defense.
🌊 Naval War
- Early U.S. naval victories (e.g., USS Constitution).
- Battle of Lake Erie (1813) – U.S. victory; “We have met the enemy and they are ours.”
🔥 Chesapeake & Southern Campaigns
- Burning of Washington (1814): British forces burned the White House and Capitol.
- Battle of Baltimore (1814): U.S. successfully defended the city; inspired “The Star-Spangled Banner.”
- Battle of New Orleans (1815): Major U.S. victory led by Andrew Jackson—fought after the peace treaty was signed (news traveled slowly).
4. How It Ended
📜 Treaty of Ghent (1814)
- Signed December 24, 1814.
- Restored pre-war borders (status quo ante bellum).
- Said nothing about impressment or neutral rights (the issues faded after Napoleon’s defeat).
5. Consequences & Significance
🇺🇸 United States
- Surge of national pride and identity.
- Andrew Jackson becomes a national hero (and later president).
- Strengthened federal authority and military confidence.
- Accelerated decline of Indigenous resistance in the Midwest.
🇨🇦 Canada
- Strengthened sense of Canadian identity.
- Reinforced resistance to U.S. annexation.
- Elevated figures like Laura Secord and Isaac Brock (who died early in the war).
🪶 Indigenous Nations
- Major loss: Britain abandoned support after the war.
- Indigenous lands increasingly seized by U.S. expansion.
🇬🇧 Britain
- Achieved its main goal: defending Canada.
- The war was a minor sideshow compared to the Napoleonic Wars.
6. Why It’s Remembered Differently
- United States: Seen as a successful defense of independence.
- Canada: Remembered as a victory that prevented U.S. conquest.
- Britain: Largely forgotten.
- Indigenous peoples: Viewed as a tragic turning point.
7. One-Sentence Summary
The War of 1812 was a messy, inconclusive conflict that nonetheless reshaped national identities in the U.S. and Canada and decisively weakened Indigenous resistance in North America.